
Companies utilizing open-source code — which is embedded in a big majority of enterprise-grade software program — want a full-scale stock of its existence. That's lacking in lots of company IT information.
And not using a detailed accounting of open-source code working inside their software program, corporations haven't any approach to monitor software program insurance policies, licenses, vulnerabilities, and variations. Meaning IT departments are clueless in regards to the total well being of the open-source elements they use.
At difficulty is that many enterprises are positive they don't use open supply, so they don't have to fret about protecting safety patches and code upgrades present. That false impression often leads to community breaches resulting in malware and ransomware assaults.
The 2022 Synopsys Open Supply Safety and Threat Evaluation (OSSRA) Report launched final month confirmed an all-time excessive in open supply code working in software program. The issue of utilizing open supply has been rising constantly yr after yr.
Open-source code is prevalent in software program packages from enterprise purposes to community and server processes. Until enterprises make a concerted effort to catalog and monitor how their organizations use open-source snippets, even recognized vulnerabilities go unattended.
Fixing the issues the report highlights is a query of possession, in keeping with Tim Mackey, principal safety strategist at Synopsys SIG.
The outcomes counsel a tacit realization that the software program powering companies may not be below their managers’ management. It additionally indicators that the open-source code in business merchandise could not meet the requirements to which they maintain their very own groups accountable.
“Given the OSSRA supply knowledge comes from technical due-diligence efforts associated to mergers and acquisitions exercise, and never a survey, the OSSRA report is a mirrored image of the present state of software program utilization and never the opinion of what it is perhaps,” Mackey informed LinuxInsider.
Harsh Truths Revealed
The 2022 OSSRA report audited anonymized findings from over 2,400 business codebases throughout 17 industries. The abstract outcomes on this graphic are a wake-up name to company IT overseers.
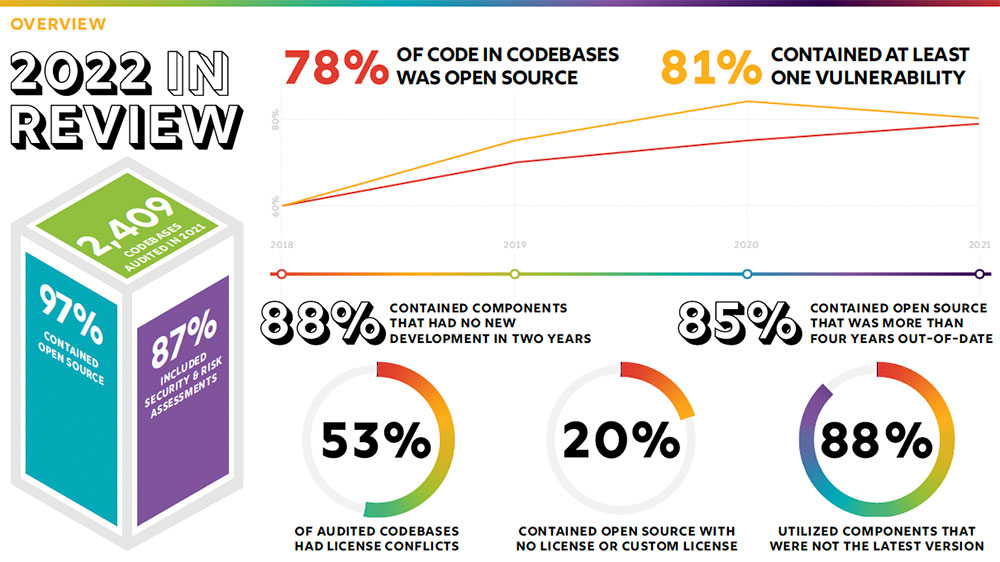
Supply: 2022 Open Supply Safety and Threat Evaluation Report (Credit score: Synopsys)
The report serves as a disaster warning, particularly in mild of the continued affect of the Log4J vulnerability that appeared late final yr.
Of the two,400 business codebases throughout 17 industries, 2,097 contained safety and operational danger assessments. The expansion within the variety of codebases Synopsys audited is 64 % bigger than final yr’s. A lot of that improve resulted from mergers and acquisitions all through 2021.
The safety threats ensuing from Log4j have been a major motive President Biden late final yr pushed his Govt Order on Cybersecurity, famous Mackey.
It was additionally key for the OSSRA report back to inspire company chief data safety officers, vice presidents of engineering, and chief technical officers to investigate their open-source software program utilization and see how properly the OSSRA knowledge maps to their very own processes and governance.
“The OSSRA report has constantly highlighted that the issue with open supply is just not throughout the open-source code itself, however in how individuals use it,” he added. “Freely downloadable code is great for the pocketbook, however that doesn't imply it may be managed utilizing the identical processes as you would possibly discover for business software program.”
SBOM No Common Repair
A key tenet of the OSSRA report is that dangers can stem from unmanaged use of open supply. The distinction is important between an absence of open-source administration and the truth that open supply itself is just not the issue, the report concludes.
Open supply now's the muse of business software program, famous researchers. It's present in 97 % of business software program. Regardless of its common use, the misperception that open supply is one way or the other inherently harmful persists.
In contrast to Microsoft and Apple merchandise, the place software program distributors can proactively push updates and patches to recognized customers, open-source has no such vendor to deal with danger administration points, noticed Mackey.
“Present patch administration options are sometimes geared towards an replace mannequin,” he added. “Software program that's freely downloadable means the software program producer doesn't know who its clients are or even when they're utilizing the software program they downloaded.
The patching course of and its assumptions get misplaced when individuals concentrate on subjects like Software program Invoice of Supplies (SBOM) being a silver bullet for open-source administration, in keeping with Mackey. Fixing the issue requires going past SBOM.
SBOM is just a device to enhance processes that have been designed for a special sort of software program consumption, he stated. As well as, industries have to concentrate on figuring out and monitoring open-source elements within the business software program they use. That's what has to occur to appropriate what the OSSRA report signifies are issues, stated Mackey.
Fixing What’s Fixable
Utilizing out of date open-source elements requires corporations to undertake a course of for monitoring when their elements change into out-of-date. However it's not simply explicitly declaring dependencies or choosing accredited suppliers. Mackey sees the issue as extra deeply rooted within the provide chain.
“The Log4Shell expertise is an ideal instance of a foundational element that few knew existed. However as soon as Log4j turned entrance of thoughts as a result of affect of the Log4Shell vulnerability, [it] compelled groups to hurry and determine how you can greatest handle it,” he identified.
That's the answer enterprise customers of business software program should do. Stock the existence of open-source elements. Then set up and execute monitoring and patching and updating.
“No matter processes these groups used to efficiently handle their Log4j expertise at scale needs to be utilized to different elements. In different phrases, use the Log4j expertise to construct a extra scalable answer on your group,” urged Mackey.
Post a Comment